An Intrusion Detection System (IDS) hardware or software program monitors a network for any hostile activities or policy infractions. A security information and event management system generally reports or gathers information about any malicious activities or violations centrally. Systems for detecting intrusions are made to be installed in various settings. Let us dive into this concept.
What is an Intrusion Detection System?
A network security tool called an intrusion detection system (IDS) was first developed to identify potential attacks against a specific program or computer. Additionally, the IDS is a listen-only gadget. An administrator receives results from the IDS’s traffic monitoring. It is unable to intervene automatically to stop an exploit from taking control of the system.
When they notice an anomaly, most IDS systems merely monitor and report suspicious activity and traffic. Some, though, can go one step further and stop malicious or suspicious traffic when they notice unusual activity. Typically, intrusion detection systems (IDS) are software programs that operate on an organization’s hardware or as a network security remedy. Additionally, cloud-based IDS solutions are available to safeguard the systems, data, and resources of enterprises within their cloud settings and deployments.

The Internet faces several difficulties in maintaining a reliable and secure system due to the vast volume of data and information it contains. While software and firewall updates help maintain security, dynamic processes can also be taken advantage of. Among the dynamic mechanisms are network analyzers and intrusion detection systems. The precise objective of detecting attacks is determined by intrusion detection.
Types of IDS
Despite serving the same function, intrusion detection systems operate a little differently from one another. There are five different IDS kinds in all.
1. Network IDS
Using one or more touchpoints, a Network Intrusion Detection System (NIDS) is a solution that keeps an eye on your whole network. Generally speaking, an NIDS must be installed on hardware that is part of your network infrastructure in order to be used. After installation, each packet that goes through your NIDS will be sampled. The traffic that passes through it can all be examined by a standard NIDS. Having said that, one might not want to examine every piece of data that passes through NIDS because one can miss an attempt at intrusion as a result of information overload.

2. Network Node IDS
Although it functions differently, we will refer to a Network Node Intrusion Detection System (NNIDS) as a distinct kind of IDS even if it is essentially a variant of an NIDS.
An NNIDS examines the packets that flow through it as well. However, the system keeps an eye on every node linked to your network, rather than depending on a single device to monitor all network activity. The system can operate more quickly since each NNIDS agent analyzes less traffic. Similarly, NNIDS consumes less system resources. It is very simple to install on your existing servers.
3. Host IDS
An enhanced version of NNIDS’s device independence is provided by a host intrusion detection system (HIDS). You can install IDS software on each device linked to your network by using a HIDS. By obtaining “snapshots” of the designated device, HIDSs function. The HIDS can find the differences that can point to an intrusion by comparing the most current snapshot to earlier recordings. HIDS has the following benefits:
- They can be set up on servers or PCs.
- They are able to identify the impacted device.
- In the event that analytical system files are altered or removed, they alert administrators.
- They work especially well against insider threats.
Unfortunately, “after-the-fact” monitoring might cause problems for HIDS solutions. Overall mean time to respond (MTTR) may be slower with HIDS solutions since many of them rely on logs that document intrusions.
4. Protocol-Based IDS
One type of IDS that keeps an eye on the protocol in use is called a Protocol-Based Intrusion Detection System (PIDS). Basically, what this system does is examine the HTTP or HTTPS protocol stream that is flowing between the server and your devices. A PIDS is often located at a server’s front end. The system can keep an eye on both inbound and outgoing traffic to safeguard your web server.

PIDSs aren’t always a complete IDS solution because of their emphasis on the protocol, or how devices send data within a network. They can, however, strengthen a cybersecurity solution that is already strong.
5. Application Protocol-Based IDS
Software application security is the focus of an IDS known as the Application Protocol-Based Intrusion Detection System (APIDS). APIDSs are typically linked to host-based intrusion detection systems (HIDS) and are used to monitor interactions between apps and servers. Usually, an APIDS is placed on a collection of servers. Similar to a PIDS, an APIDS is unlikely to meet all of your requirements for network monitoring. Nevertheless, it can work well with different IDS models.
Intrusion Detection System Model
The important features for the categorization are chosen using the feature selection approach. A dataset that contains only the most important features improves the model’s acceptability and accuracy. The classifiers are then trained using the set of notable features. Following classifier training, the test dataset is examined to determine if each individual occurrence represents an attack or normal data using the same set of attributes.
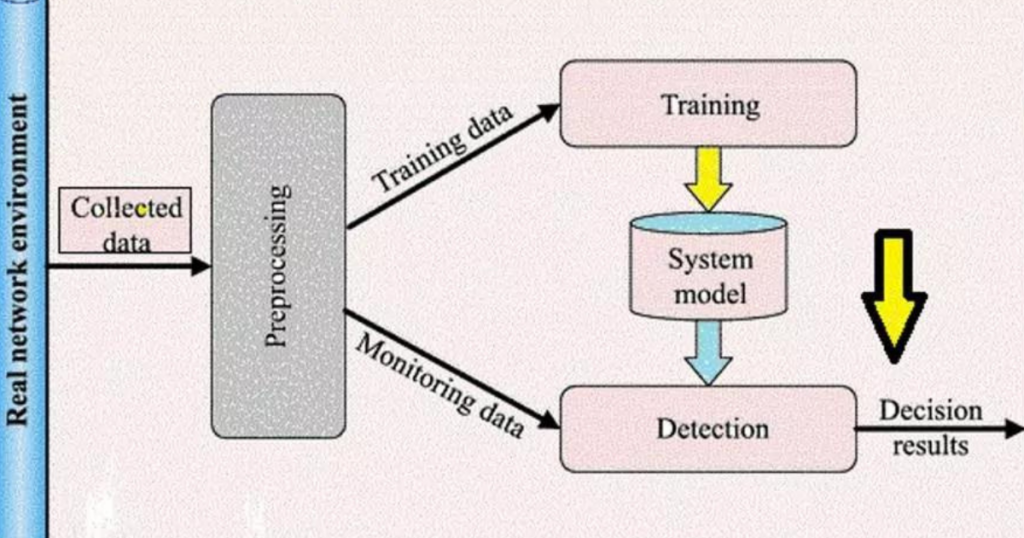
- Data Collection: Compile a sizable amount of information about both typical and unusual activity on your system or network.
- Feature Selection: Find pertinent characteristics or features in the data that can aid in differentiating between malicious and legitimate activity. These might include things like network traffic, system resource utilization, or login habits.
- Training Phase: Utilize the historical data to train the system using a machine learning technique. The program gains the ability to identify patterns linked to both possible invasions and typical activity.
- Testing and Evaluation: Assess the trained model with an independent, previously untrained set of data. This makes it more likely that the model will detect abnormalities correctly and generalize well.
Machine Learning Methods
1. Decision Tree
A non-parametric supervised machine learning model called Decision Tree is used for both regression and classification applications. It divides the data according to a particular attribute repeatedly. The decision rules that are inferred from the data attributes are taught to the decision tree. It forecasts the target variable’s value based on those rules. This model’s decision-making process can be interpreted more easily by the user when it is fashioned like a tree. The output of DT can be visualized using a wide range of machine-learning methods.
2. Adaptive Boosting
This is an approach to group learning that makes use of an iterative process to help weaker learners correct their mistakes. To improve the model’s performance, it continually calls a weak learner or a specified base learning algorithm, for an intrusion detection system over the course of several rounds. Reassigning weights to each instance and assigning bigger weights to instances that were incorrectly classified is the core idea behind AdaBoost. By increasing the weight of training instances that are mistakenly classified, the second classifier is trained. Then, using the updated weights, it makes another prediction on the training set. Next, change the instance weights once more, and so forth.
3. Multilayer Perceptron
is an Artificial Neural Network (ANN) that is feed-forward, meaning that information is passed forward from input to output. The input layer, hidden layer, and output layer are the three layers of nodes that make up a multilayer perceptron, as the name would imply. But in an MLP, every node—aside from the input unit—is a neuron, and these neurons convert the weighted sum of the input into output by means of a nonlinear activation function. The input layer receives the input signal, and the output layer performs the desired task, such as classification or regression.
Observations
The IDS’s effectiveness is mostly dependent on training with the right dataset. To improve results, an algorithm can be trained with a short dataset for machine learning models. However, machine learning is not appropriate for larger datasets unless they are labeled. intrusion detection system must be routinely educated using fresh data gathered from network traffic monitoring in order to become effective in identifying zero-day attacks.
This demonstrates how frequently the researchers use ML-based algorithms when creating an effective intrusion detection solution.
Intrusion Detection & Machine Learning
Experimental results, however, demonstrate that the precision of current learning techniques is insufficient to identify the kinds of anomalies. It is costly to generate an appropriately labeled data set that is representative of all types of behaviors because labeling is frequently done manually by human experts. Thus, three operating modes for anomaly detection techniques—Supervised Learning, Unsupervised Learning, and Semi-supervised Learning—are identified based on the availability of the labels.
Importance

- Intrusion detection systems can change and adapt to the evolving nature of cyber threats thanks to machine learning. New and complex attack strategies may be too much for traditional rule-based systems to handle, but machine learning algorithms are able to recognize patterns even in data that has never been seen before.
- Anomaly detection, which is essential for spotting odd patterns or behaviors in network traffic, is an area where machine learning shines. Anomalies could point to possible security lapses that are hard to find with rule-based systems by themselves.
- By analyzing typical network behavior, machine learning (ML) makes it possible to identify departures from this baseline. ML algorithms can detect anomalous actions that could be signs of an intrusion by learning what defines “normal” behavior.
- ML can lessen false positives by recognizing typical fluctuations in network traffic and the context. This is especially crucial in large-scale, intricate networks where a high volume of false alarms could be produced by conventional methods.
- ML algorithms are proficient in identifying intricate correlations and patterns in data. This feature enables the identification of well-known attack patterns and the discovery of novel attack vectors within the context of intrusion detection systems.
- ML models are capable of ongoing learning and environment adaptation to changes in the network. This is necessary to keep the intrusion detection system effective over time because it allows it to improve its understanding of harmful and normal behavior by learning from new data.
Conclusion
The network size and related data have greatly increased as a result of the quick developments in the internet and communication areas. As a result, a lot of new attacks are developed, which has made it difficult for network security to precisely identify breaches. One such technology is an intrusion detection system (IDS), which guards against potential network invasions by examining network traffic to guarantee its availability, confidentiality, and integrity. IDS still has difficulties identifying new intrusions, lowering false alarm rates, and increasing detection accuracy despite the researchers’ tremendous efforts.
IDS systems based on machine learning (ML) and deep learning (DL) are being used more frequently as viable remedies to effectively identify intrusions throughout networks. By offering a dynamic and adaptable approach to threat detection, early anomaly identification, less false positives, and enhanced overall protection against ever-evolving cyber threats, machine learning (ML) augments the capabilities of intrusion detection systems.

